Spring Security 密碼驗(yàn)證動(dòng)態(tài)加鹽的驗(yàn)證處理方法
本文個(gè)人博客地址:https://www.leafage.top/posts/detail/21697I2R
最近幾天在改造項(xiàng)目,需要將gateway整合security在一起進(jìn)行認(rèn)證和鑒權(quán),之前gateway和auth是兩個(gè)服務(wù),auth是shiro寫(xiě)的一個(gè),一個(gè)filter和一個(gè)配置,內(nèi)容很簡(jiǎn)單,生成token,驗(yàn)證token,沒(méi)有其他的安全檢查,然后讓對(duì)項(xiàng)目進(jìn)行重構(gòu)。
先是要整合gateway和shiro,然而因?yàn)間ateway是webflux,而shiro-spring是webmvc,所以沒(méi)搞成功,如果有做過(guò)并成功的,請(qǐng)告訴我如何進(jìn)行整合,非常感謝。
那整合security呢,因?yàn)閟pring cloud gateway基于webflux,所以網(wǎng)上很多教程是用不了的,webflux的配置會(huì)有一些變化,具體看如下代碼示例:
import io.leafage.gateway.api.HypervisorApi;import io.leafage.gateway.handler.ServerFailureHandler;import io.leafage.gateway.handler.ServerSuccessHandler;import io.leafage.gateway.service.JdbcReactiveUserDetailsService;import org.springframework.context.annotation.Bean;import org.springframework.http.HttpMethod;import org.springframework.http.HttpStatus;import org.springframework.security.config.annotation.web.reactive.EnableWebFluxSecurity;import org.springframework.security.config.web.server.ServerHttpSecurity;import org.springframework.security.core.userdetails.ReactiveUserDetailsService;import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;import org.springframework.security.crypto.password.PasswordEncoder;import org.springframework.security.web.server.SecurityWebFilterChain;import org.springframework.security.web.server.authentication.HttpStatusServerEntryPoint;import org.springframework.security.web.server.authentication.ServerAuthenticationFailureHandler;import org.springframework.security.web.server.authentication.ServerAuthenticationSuccessHandler;import org.springframework.security.web.server.authentication.logout.HttpStatusReturningServerLogoutSuccessHandler;import org.springframework.security.web.server.csrf.CookieServerCsrfTokenRepository;/** * spring security config . * * @author liwenqiang 2019/7/12 17:51 */@EnableWebFluxSecuritypublic class ServerSecurityConfiguration { // 用于獲取遠(yuǎn)程數(shù)據(jù) private final HypervisorApi hypervisorApi; public ServerSecurityConfiguration(HypervisorApi hypervisorApi) {this.hypervisorApi = hypervisorApi; } /** * 密碼配置,使用BCryptPasswordEncoder * * @return BCryptPasswordEncoder 加密方式 */ @Bean protected PasswordEncoder passwordEncoder() {return new BCryptPasswordEncoder(); } /** * 用戶(hù)數(shù)據(jù)加載 * * @return JdbcReactiveUserDetailsService 接口 */ @Bean public ReactiveUserDetailsService userDetailsService() {// 自定義的ReactiveUserDetails 實(shí)現(xiàn)return new JdbcReactiveUserDetailsService(hypervisorApi); } /** * 安全配置 */ @Bean SecurityWebFilterChain springSecurityFilterChain(ServerHttpSecurity http) {http.formLogin(f -> f.authenticationSuccessHandler(authenticationSuccessHandler()).authenticationFailureHandler(authenticationFailureHandler())).logout(l -> l.logoutSuccessHandler(new HttpStatusReturningServerLogoutSuccessHandler())).csrf(c -> c.csrfTokenRepository(CookieServerCsrfTokenRepository.withHttpOnlyFalse())).authorizeExchange(a -> a.pathMatchers(HttpMethod.OPTIONS).permitAll().anyExchange().authenticated()).exceptionHandling(e -> e.authenticationEntryPoint(new HttpStatusServerEntryPoint(HttpStatus.UNAUTHORIZED)));return http.build(); } /** * 登陸成功后執(zhí)行的處理器 */ private ServerAuthenticationSuccessHandler authenticationSuccessHandler() {return new ServerSuccessHandler(); } /** * 登陸失敗后執(zhí)行的處理器 */ private ServerAuthenticationFailureHandler authenticationFailureHandler() {return new ServerFailureHandler(); }}
上面的示例代碼,是我開(kāi)源項(xiàng)目中的一段,一般的配置就如上面寫(xiě)的,就可以使用了,但是由于我們之前的項(xiàng)目中的是shiro,然后有一個(gè)自定義的加密解密的邏輯。
首先說(shuō)明一下情況,之前那一套加密(前端MD5,不加鹽,然后數(shù)據(jù)庫(kù)存儲(chǔ)的是加鹽后的數(shù)據(jù)和對(duì)應(yīng)的鹽(每個(gè)賬號(hào)一個(gè)),要登錄比較之前對(duì)密碼要獲取動(dòng)態(tài)的鹽,然后加鹽進(jìn)行MD5,再進(jìn)行對(duì)比,但是在配置的時(shí)候是沒(méi)法獲取某一用戶(hù)的鹽值)
所以上面的一版配置是沒(méi)法通過(guò)驗(yàn)證的,必須在驗(yàn)證之前,給請(qǐng)求的密碼混合該賬號(hào)對(duì)應(yīng)的鹽進(jìn)行二次加密后在對(duì)比,但是這里就有問(wèn)題了:
security 框架提供的幾個(gè)加密解密工具沒(méi)有MD5的方式; security 配置加密解密方式的時(shí)候,無(wú)法填入動(dòng)態(tài)的賬號(hào)的加密鹽;對(duì)于第一個(gè)問(wèn)題還好處理,解決方式是:自定義加密解密方式,然后注入到配置類(lèi)中,示例如下:
import cn.hutool.crypto.SecureUtil;import com.ichinae.imis.gateway.utils.SaltUtil;import org.springframework.security.crypto.codec.Utf8;import org.springframework.security.crypto.password.PasswordEncoder;import java.security.MessageDigest;/** * 自定義加密解密 */public class MD5PasswordEncoder implements PasswordEncoder { @Override public String encode(CharSequence charSequence) {String salt = SaltUtil.generateSalt();return SecureUtil.md5(SecureUtil.md5(charSequence.toString()) + salt); } @Override public boolean matches(CharSequence charSequence, String encodedPassword) {byte[] expectedBytes = bytesUtf8(charSequence.toString());byte[] actualBytes = bytesUtf8(charSequence.toString());return MessageDigest.isEqual(expectedBytes, actualBytes); } private static byte[] bytesUtf8(String s) {// need to check if Utf8.encode() runs in constant time (probably not).// This may leak length of string.return (s != null) ? Utf8.encode(s) : null; }}
第二個(gè)問(wèn)題的解決辦法,找了很多資料,也沒(méi)有找到,后來(lái)查看security的源碼發(fā)現(xiàn),可以在UserDetailsService接口的findByUsername()方法中,在返回UserDetails實(shí)現(xiàn)的時(shí)候,使用默認(rèn)實(shí)現(xiàn)User的UserBuilder內(nèi)部類(lèi)來(lái)解決這個(gè)問(wèn)題,因?yàn)閁serBuilder類(lèi)中有一個(gè)屬性,passwordEncoder屬性,它是Fucntion<String, String>類(lèi)型的,默認(rèn)實(shí)現(xiàn)是 password -> password,即對(duì)密碼不做任何處理,先看下它的源碼:
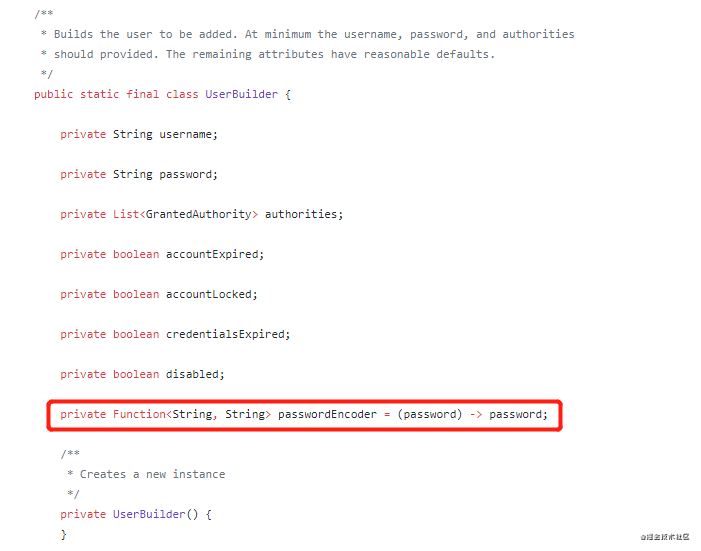
再看下解決問(wèn)題之前的findByUsername()方法:
@Servicepublic class UserDetailsServiceImpl implements ReactiveUserDetailsService { @Resource private RemoteService remoteService; @Override public Mono<UserDetails> findByUsername(String username) {return remoteService.getUser(username).map(userBO -> User.builder().username(username).password(userBO.getPassword()).authorities(grantedAuthorities(userBO.getAuthorities())).build()); } private Set<GrantedAuthority> grantedAuthorities(Set<String> authorities) {return authorities.stream().map(SimpleGrantedAuthority::new).collect(Collectors.toSet()); }}
那找到了問(wèn)題的解決方法,就來(lái)改代碼了,如下所示:
新增一個(gè)代碼處理方法
private Function<String, String> passwordEncoder(String salt) { return rawPassword -> SecureUtil.md5(rawPassword + salt);}
然后添加builder鏈
@Servicepublic class UserDetailsServiceImpl implements ReactiveUserDetailsService { @Resource private RemoteService remoteService; @Override public Mono<UserDetails> findByUsername(String username) {return remoteService.getUser(username).map(userBO -> User.builder().passwordEncoder(passwordEncoder(userBO.getSalt())) //在這里設(shè)置動(dòng)態(tài)的鹽.username(username).password(userBO.getPassword()).authorities(grantedAuthorities(userBO.getAuthorities())).build()); } private Set<GrantedAuthority> grantedAuthorities(Set<String> authorities) {return authorities.stream().map(SimpleGrantedAuthority::new).collect(Collectors.toSet()); } private Function<String, String> passwordEncoder(String salt) {return rawPassword -> SecureUtil.md5(rawPassword + salt); }}
然后跑一下代碼,請(qǐng)求登錄接口,就登陸成功了。
以上就是Spring Security 密碼驗(yàn)證動(dòng)態(tài)加鹽的驗(yàn)證處理的詳細(xì)內(nèi)容,更多關(guān)于Spring Security密碼驗(yàn)證的資料請(qǐng)關(guān)注好吧啦網(wǎng)其它相關(guān)文章!
相關(guān)文章:
1. Python的文本常量與字符串模板之string庫(kù)2. Python+unittest+requests 接口自動(dòng)化測(cè)試框架搭建教程3. jsp+servlet簡(jiǎn)單實(shí)現(xiàn)上傳文件功能(保存目錄改進(jìn))4. 存儲(chǔ)于xml中需要的HTML轉(zhuǎn)義代碼5. 完美解決vue 中多個(gè)echarts圖表自適應(yīng)的問(wèn)題6. 利用CSS制作3D動(dòng)畫(huà)7. 一款功能強(qiáng)大的markdown編輯器tui.editor使用示例詳解8. .Net加密神器Eazfuscator.NET?2023.2?最新版使用教程9. Java GZip 基于內(nèi)存實(shí)現(xiàn)壓縮和解壓的方法10. SpringBoot+TestNG單元測(cè)試的實(shí)現(xiàn)

 網(wǎng)公網(wǎng)安備
網(wǎng)公網(wǎng)安備